Embracing Zero-Trust Cybersecurity
A Comprehensive Approach to Protecting and Enhancing
Resilience of the Modern Organization
The Evolution of Cybersecurity
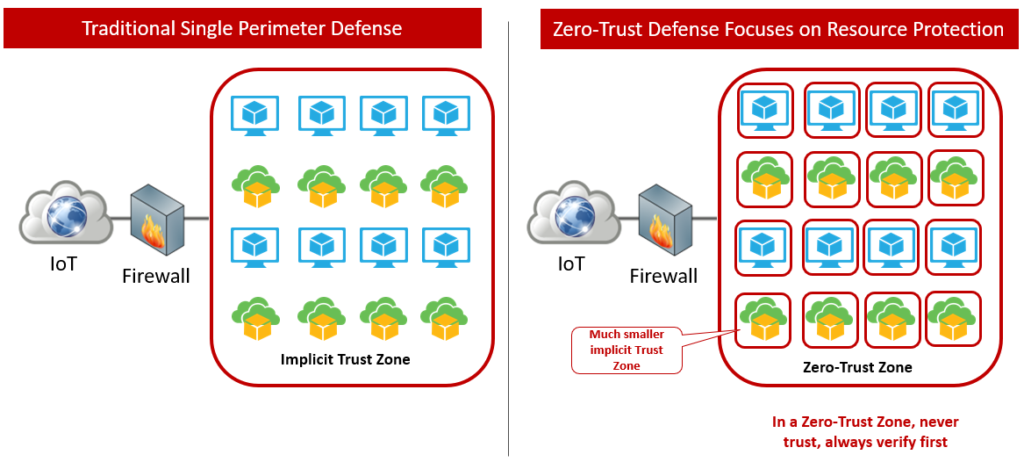
In today’s interconnected world, where data breaches and cyberattacks have become commonplace, traditional perimeter-based security measures are no longer sufficient to protect organizations from advanced threats. Advanced Persistent Threats (APTs) and insider threats have demonstrated that the traditional approach is no longer effective. The consequences of a breach in this context can be devastating, leading to data theft, financial losses, and reputational damage. The need for a more robust and adaptable approach to cybersecurity has led to the rise of the Zero-Trust approach.
The Zero-Trust approach challenges the conventional wisdom of “trust but verify” by assuming that no entity, whether inside or outside the network, can be trusted implicitly. Instead, it advocates the complete abandonment of the implicit trust in any entity, whether inside or outside an organization’s network. This approach assumes that no device, user, or application can be trusted by default, and every access request must be authenticated, authorized, and continuously monitored, regardless of its source.
The Zero-Trust Approach: Unravelling the Core Principles
Zero-Trust is not just another buzzword , it’s a comprehensive and adaptable security framework designed to address the evolving threat landscape. To understand the Zero-Trust approach better, let’s delve into its core principles:
- Never Trust, Always Verify: The fundamental premise of Zero-Trust is to reject the assumption that anything, or anyone, is inherently trustworthy. Instead, it promotes continuous verification of every user, device, application, and network connection trying to access resources within the network. Users and devices must authenticate themselves before gaining access to resources. Multi-factor authentication (MFA) is commonly used to strengthen identity verification.
- Least Privilege Access: Zero-Trust minimizes the privileges granted to users and devices. Users are only given access to the resources necessary for their job, limiting lateral movement within the network for potential attackers. Access privileges are granted on a need-to-know basis. Users and systems only receive the minimum permissions necessary to perform their tasks.
- Micro-Segmentation: In a Zero-Trust architecture, the network is divided into smaller segments, each with specific security policies. This way, even if a breach occurs in one segment, it is contained, preventing lateral movement.
- Real-time Monitoring: Continuous monitoring of user and device behavior, network traffic, and system activity is a cornerstone of Zero-Trust. Any deviations from the established norms trigger alerts and potential security responses.
- Contextual Access Control: Access decisions are based on contextual information, such as user identity, device health, location, and the sensitivity of the data or resource being accessed. Access is dynamically adjusted based on changing conditions. All access requests are explicitly approved or denied based on policies, not based on trust or location.
To implement a Zero-Trust cybersecurity approach, organizations need to consider several key components and strategies:
- Identity and Access Management (IAM): A robust IAM system is essential for verifying the identity of users and devices. It includes Single Sign-On (SSO), Multi-Factor Authentication (MFA), and role-based access control.
- Network Micro-Segmentation: This involves dividing the network into smaller, isolated segments or zones. Each segment can have its own set of access controls and security policies, reducing the lateral movement of threats.
- Security Analytics and Threat Detection: Utilizing advanced security analytics and machine learning, organizations can continuously monitor network traffic and user behavior to detect anomalies and potential threats in real-time.
- Application Security: Applications must be secured at the code level, and access should be controlled based on a user’s privileges and the least privilege principle.
- Secure Access Service Edge (SASE): SASE is an emerging technology integrating network security and Wide-Area Networking (WAN) capabilities. It extends Zero-Trust principles to remote users and cloud services.
Benefits of Zero-Trust
Implementing a Zero-Trust approach offers numerous advantages that significantly enhance an organization’s security posture:
- Minimized Attack Surface: The attack surface is significantly reduced by implementing least privilege access and micro-segmentation. Attackers have difficulty moving laterally within the network and accessing critical assets.
- Improved Data Protection: Zero-Trust ensures that sensitive data is protected from unauthorized access. Access controls adapt to changing conditions and user behavior in real time, reducing the risk of data breaches.
- Enhanced Security Posture: The continuous monitoring and real-time access control provided by Zero-Trust allow organizations to respond to threats quickly and effectively. This proactive approach to security minimizes the impact of potential breaches.
- Adaptability: Zero-Trust is scalable and can be tailored to an organization’s needs. Whether a small business or a large organization, the principles of Zero-Trust can be applied effectively.
- Compliance Alignment and Risk Mitigation: Many industry regulations and standards, such as the General Data Protection Regulation (GDPR), require organizations to implement strong security controls. Zero-Trust helps organizations align with these compliance requirements. Organizations adopting a Zero-Trust model can better protect sensitive data and reduce the risk of data breaches and associated financial and reputational damage.
- User-Friendly: Despite its robust security measures, Zero-Trust can be implemented to minimize disruption to user experiences, ensuring that security doesn’t hinder productivity
Challenges in Implementing Zero-Trust
While the benefits of a Zero-Trust approach are compelling, implementing it is not without its challenges:
- Complexity: Transitioning to a Zero-Trust architecture can be complex and disruptive. It may require changes in infrastructure, policies, and a cultural shift within the organization. Organizations must carefully plan and execute this transition to avoid service disruptions.
- Integration: Integrating Zero-Trust into existing systems and processes can be challenging. Legacy systems may not easily support the principles of Zero-Trust, requiring additional investments in technology and training.
- User Experience: The strict access controls and continuous verification can sometimes hinder user experience. Organizations must strike a balance between security and usability.
- Cost: The initial investment in Zero-Trust technology and training can be high, particularly for smaller organizations with limited resources. The investment in new technologies and training can be significant. However, the long-term benefits often outweigh the upfront costs.
- Change Management: Adopting a Zero-Trust approach often requires a cultural shift within the organization. Employees may resist additional security measures, such as MFA and more frequent authentication requests, which can slow their workflow. Employees need to understand and embrace the new security mindset.
- Skill Shortages: Finding and retaining cybersecurity professionals with expertise in Zero-Trust can be challenging, as the demand for these skills is rising.
Zero-Trust in Action: Practical Use Cases
To illustrate the real-world applications of Zero-Trust, consider a few use cases where organizations can successfully adopt this approach:
- Cloud Security: As more organizations migrate their services to the cloud, Zero-Trust provides a secure way to access cloud resources. Users and devices are continuously authenticated and authorized before connecting to cloud-based applications and data.
- Remote Work: The rise of remote work has created new security challenges. Zero-Trust allows organizations to secure remote access to corporate resources, ensuring that only authorized users with the proper credentials can access sensitive data and applications.
- Mobile Device Security: In the age of “Bring Your Own Device” (BYOD), Zero-Trust helps organizations secure mobile devices. Users are authenticated, and their devices are checked for compliance with security policies before accessing corporate resources.
- Insider Threat Mitigation: Zero-Trust is effective in mitigating insider threats. Employees with valid credentials are continuously monitored to detect unusual behaviour or data access, reducing the risk of insider data breaches.
- Network Security: Traditional network security often relies on perimeter defences. Zero-Trust takes a more holistic approach by applying security controls at the network level, with real-time monitoring and access control.
- IoT Security: The proliferation of IoT devices presents new security challenges. Zero-Trust can help by ensuring that IoT devices are authenticated, authorized, and segregated from critical systems to prevent potential threats.
As the cybersecurity landscape continues to evolve, Zero-Trust is expected to become the standard approach for securing organizations of all sizes. The principles of least privilege, continuous monitoring, and strict access control will remain central to safeguarding against cyber threats. Additionally, the following trends will likely shape the future of Zero-Trust:
- Identity and Access Management (IAM) Solutions: IAM solutions are crucial in verifying user identities and enforcing access policies. They are integral to Zero-Trust architecture.
- Integration with Artificial Intelligence (AI) and Machine Learning (ML): AI and ML will play a more significant role in threat detection and anomaly identification within the Zero-Trust framework.
- Blockchain: Blockchain can be used to create a tamper-proof audit trail of access and changes to sensitive data. This ensures data integrity and accountability within a Zero-Trust network.
- Software-Defined Perimeter (SDP): SDP solutions create a secure and isolated network overlay, ensuring that only authorized users and devices can access network resources. This technology simplifies the implementation of Zero-Trust principles.
- Convergence of Network and Security: Zero-Trust and security networking will merge further, with solutions like Secure Access Service Edge (SASE) becoming more prevalent.
- Industry-Specific Adoption: Different industries like insurance, healthcare, banking, and finance will tailor their Zero-Trust implementations to meet their specific regulatory and security requirements.
- Zero-Trust as a Service: Managed service providers will offer Zero-Trust to help organizations implement and maintain this complex security model.
- User Education: Increasing user awareness and education on Zero-Trust principles will be essential to minimize user resistance and ensure successful adoption.
In today’s digital age, organizations need to adopt and adapt to the principles of Zero-Trust to safeguard their valuable assets and ensure their continued success. Zero-Trust is a buzzword and a strategic approach to cybersecurity, becoming the standard for modern organizations facing ever-evolving cyber threats.
While implementing Zero-Trust can be challenging and complex, the benefits, including enhanced security, improved compliance, and risk mitigation, make it a worthwhile investment. Many successful organizations are already reaping the rewards of this approach and maintaining the trust of their customers and stakeholders in an increasingly digital and interconnected world.


